A Brief History of Cybersecurity Attacks on Operational Technology
In today’s interconnected world, the convergence of operational technology (OT) and information technology (IT) has brought numerous benefits, but it has also introduced new risks. The history of cybersecurity attacks on OT systems is a testament to the evolving nature of cyber threats and the increasing importance of securing critical infrastructure.
The early days of OT security were marked by a lack of awareness and understanding of cyber threats. OT systems, which control physical processes such as manufacturing, transportation, and energy production, were traditionally isolated from external networks and considered immune to cyber attacks. However, this perception changed with the rise of interconnected industrial networks and the Internet of Things (IoT).
One of the earliest recorded OT attacks occurred in 2000 when the infamous “ILOVEYOU” virus spread globally, affecting millions of computers and causing significant damage to businesses. While this attack primarily targeted IT systems, it highlighted the potential impact of cyber threats on critical infrastructure.
In the following years, as OT systems became more interconnected and reliant on IT networks, the frequency and sophistication of cyber attacks increased. Stuxnet, discovered in 2010, was a groundbreaking cyber weapon designed to target Iran’s nuclear program by sabotaging its industrial control systems. This attack demonstrated the capability of malware to cause physical damage to OT infrastructure, marking a significant shift in the cyber threat landscape.
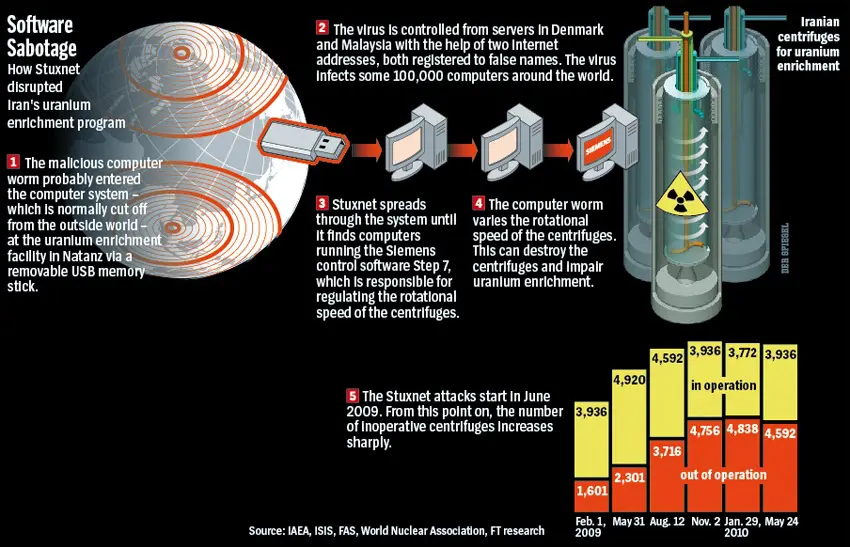
Subsequent attacks, such as the 2015 Ukraine power grid attack and the 2017 WannaCry ransomware outbreak, further underscored the vulnerability of OT systems to cyber threats. These incidents highlighted the need for improved cybersecurity measures to protect critical infrastructure from malicious actors seeking to disrupt operations or cause physical harm.
In recent years, the convergence of IT and OT has accelerated, driven by digital transformation initiatives and the adoption of Industry 4.0 technologies. This convergence has created new opportunities for efficiency and innovation but has also expanded the attack surface for cyber threats. As a result, securing OT systems has become a top priority for organizations across industries, leading to the development of specialized cybersecurity solutions tailored to the unique requirements of industrial environments.
Looking ahead, the history of cybersecurity attacks on OT serves as a reminder of the ongoing challenges posed by cyber threats in an increasingly interconnected world. As technology continues to advance, the need for robust OT security measures will only grow, requiring collaboration between industry stakeholders, government agencies, and cybersecurity experts to ensure the resilience of critical infrastructure against evolving cyber threats.
At Technon Cyber, we bring years of experience in the fields of security, intelligence, cybersecurity, OT/ICS security and decision making. This experience stems from the security challenges faced by both the State of Israel and the United States of America in recent decades. Technon consultants are men and women that had an important role in the resolution of those challenges. We have a unique edge when it comes to understanding current threats to your operational environment (critical infrastructure, manufacturing, etc.), and how to mitigate them, strengthening your organization’s overall resilience.
For more information and to schedule a call with us visit: www.TechnonCyber.com

Article written by Technon Cyber.



